Real gaming router
Real gaming router
https://kittenlabs.de/real-gaming-router/
Running GTA: Vice City on a TP-Link TL-WDR4900 wireless router

Cracking Meta’s Messenger Certificate Pinning on macOS
Cracking Meta’s Messenger Certificate Pinning on macOS
https://texts.blog/2024/02/20/cracking-metas-messenger-certificate-pinning-on-macos/
Bypassing certificate pinning in Meta’s Messenger application on macOS.

World Server Throwing Championship
World Server Throwing Championship
https://www.cloudfest.com/world-server-throwing-championship
The World Server Throwing Championship at CloudFest lets Cloud professionals demonstrate their raw power! Are you strong enough?

Ramrecovery: Simple demo illustrating remanence of data in RAM (see Cold boot attack) using a Raspberry Pi
GitHub - anfractuosity/ramrecovery: Simple demo illustrating remanence of data in RAM (see Cold boot attack) using a Raspberry Pi. Loads many images of the Mona Lisa into RAM and recovers after powering off/on again.
https://github.com/anfractuosity/ramrecovery
Simple demo illustrating remanence of data in RAM (see Cold boot attack) using a Raspberry Pi. Loads many images of the Mona Lisa into RAM and recovers after powering off/on again. - GitHub - anfr...

DEF CON 30 - Sam Bent - Tor - Darknet Opsec By a Veteran Darknet Vendor
DEF CON 30 - Sam Bent - Tor - Darknet Opsec By a Veteran Darknet Vendor
https://www.youtube.com/watch?v=01oeaBb85Xc
The hacking subculture's closest relative is that of the Darknet. Both have knowledgeable people, many of whom are highly proficient with technology and wish...
Visualizing ext4
Visualizing ext4
https://buredoranna.github.io/linux/ext4/2020/01/09/ext4-viz.html
What does ext4 look like?
How I forked SteamOS for my living room PC
https://iliana.fyi/blog/build-your-own-steamos-updates/
Interesting double-poly latches inside AMD's vintage LANCE Ethernet chip
Interesting double-poly latches inside AMD's vintage LANCE Ethernet chip
https://www.righto.com/2023/12/amd-lance-ethernet-double-poly.html
I've studied a lot of chips from the 1970s and 1980s, so I usually know what to expect. But an Ethernet chip from 1982 had something new: a ...
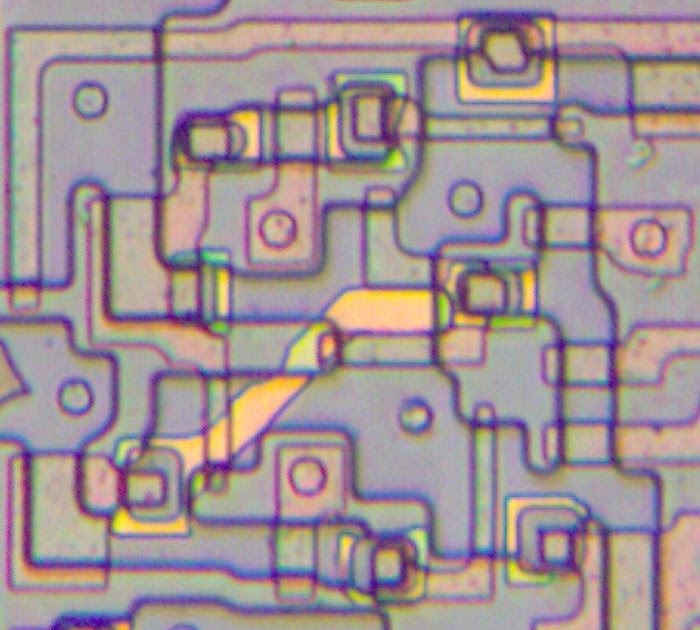
Operation Triangulation: The last (hardware) mystery
Operation Triangulation: The last (hardware) mystery
https://securelist.com/operation-triangulation-the-last-hardware-mystery/111669/
Recent iPhone models have additional hardware-based security protection for sensitive regions of the kernel memory. We discovered that to bypass this hardware-based security protection, the attackers used another hardware feature of Apple-designed SoCs.