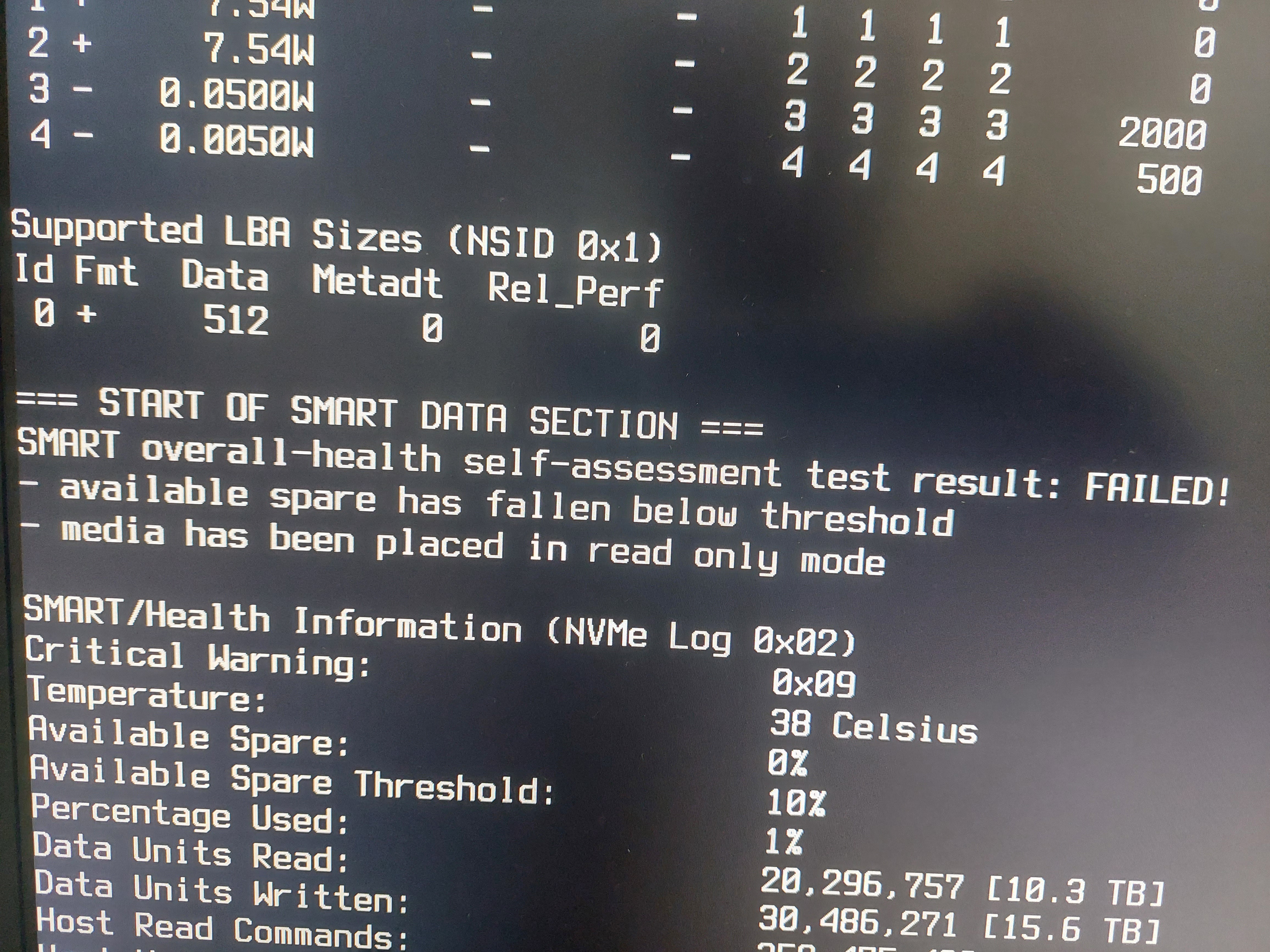
What are you favourite/useful rsync tricks these days?
Mine is rsync -r --chown=AUSER:AGROUP SRC DST to copy the files and change the ownership on the fly.
Happy 50th birthday, Ethernet | APNIC Blog
https://blog.apnic.net/2023/06/29/happy-50th-birthday-ethernet/
Why has Ethernet endured as a ubiquitous data framing protocol over all these years?

It started off with an employee sending an email to a distribution list called "Bedlam DL3" asking to be taken off the list. With 13,000 recipients and everyone replying all with, "Me too!" and other messages, it was estimated that over 15 million messages were sent through the system in an hour. This crashed the MTA service due to a recipient limit. Each time the MTA service recovered, it would attempt to resend the message again which lead to a crash loop.
As a result of the incident, the Exchange team introduced message recipient limits and distribution list restrictions to Exchange, which is something we all use today!
More on the story here: https://techcommunity.microsoft.com/t5/exchange-team-blog/me-too/ba-p/610643
cross-posted from: https://techy.news/post/2224
Looks like OWA is down for some users, the rest of the O365 apps appear to be fine.
Monitoring is a Pain
https://matduggan.com/were-all-doing-metrics-wrong/
And we're all doing it wrong (including me) I have a confession. Despite having been hired multiple times in part due to my experience with monitoring platforms, I have come to hate monitoring. Monitoring and observability tools commit the cardinal sin of tricking people into thinking this is an easy
Hey like the title says I'm looking for a way to keep up with outages and vulnerabilities. I mostly used r/sysadmin to alert me to things, but given everything I don't want to go to reddit if I don't have to.
If I can have my preference I just want one point to check at least until the numbers build up here and it becomes the go to place for that info. Anybody know of anything?
New vCenter Security Vulnerability
Support Content Notification - Support Portal - Broadcom support portal
https://www.vmware.com/security/advisories/VMSA-2023-0014.html
cross-posted from: https://lemmy.run/post/10475
Testing Service Accounts in Kubernetes
Service accounts in Kubernetes are used to provide a secure way for applications and services to authenticate and interact with the Kubernetes API. Testing service accounts ensures their functionality and security. In this guide, we will explore different methods to test service accounts in Kubernetes.
1. Verifying Service Account Existence
To start testing service accounts, you first need to ensure they exist in your Kubernetes cluster. You can use the following command to list all the available service accounts:
kubectl get serviceaccountsVerify that the service account you want to test is present in the output. If it's missing, you may need to create it using a YAML manifest or the
kubectl create serviceaccountcommand.2. Checking Service Account Permissions
After confirming the existence of the service account, the next step is to verify its permissions. Service accounts in Kubernetes are associated with roles or cluster roles, which define what resources and actions they can access.
To check the permissions of a service account, you can use the
kubectl auth can-icommand. For example, to check if a service account can create pods, run:kubectl auth can-i create pods --as=system:serviceaccount:<namespace>:<service-account>Replace
<namespace>with the desired namespace and<service-account>with the name of the service account.3. Testing Service Account Authentication
Service accounts authenticate with the Kubernetes API using bearer tokens. To test service account authentication, you can manually retrieve the token associated with the service account and use it to authenticate requests.
To get the token for a service account, run:
kubectl get secret <service-account-token-secret> -o jsonpath="{.data.token}" | base64 --decodeReplace
<service-account-token-secret>with the actual name of the secret associated with the service account. This command decodes and outputs the service account token.You can then use the obtained token to authenticate requests to the Kubernetes API, for example, by including it in the
Authorizationheader using tools likecurlor writing a simple program.4. Testing Service Account RBAC Policies
Role-Based Access Control (RBAC) policies govern the access permissions for service accounts. It's crucial to test these policies to ensure service accounts have the appropriate level of access.
One way to test RBAC policies is by creating a Pod that uses the service account you want to test and attempting to perform actions that the service account should or shouldn't be allowed to do. Observe the behavior and verify if the access is granted or denied as expected.
5. Automated Testing
To streamline the testing process, you can create automated tests using testing frameworks and tools specific to Kubernetes. For example, the Kubernetes Test Framework (KTF) provides a set of libraries and utilities for writing tests for Kubernetes components, including service accounts.
Using such frameworks allows you to write comprehensive test cases to validate service account behavior, permissions, and RBAC policies automatically.
Conclusion
Testing service accounts in Kubernetes ensures their proper functioning and adherence to security policies. By verifying service account existence, checking permissions, testing authentication, and validating RBAC policies, you can confidently use and rely on service accounts in your Kubernetes deployments.
Remember, service accounts are a critical security component, so it's important to regularly test and review their configuration to prevent unauthorized access and potential security breaches.